Origination controller¶
Origination controller detect sudden splashes of originated traffic and informs administrator when it happens.
This control is needed when performing services to untrusted clients.
There are known cases, when intruders hack your originator, for example, by SIP password brute-force.
After this intruders terminate to your hacked client big amount of traffic, which comes to your switch.
On your switch this traffic is seen as a regular traffic from your originator, however bigger, than usual, volume or to more expensive destinations.
Usually this happens at night time when no one is able to detect the intrusion.
Attacks which could be prevented by Origination controller:
- A hack of your partner-originator and launch of parallel VoIP proxy
- Password brute-force of your originator
- Stolen password
When billing time comes, the hacked client might refuse to pay the invoices, saying that he didn't send the traffic.
Or client might refuse to pay due to bankruptcy which is caused by the intrusion.
For Smartswitch owner it's important to prevent this situation.
For this purpose origination controller could be used.
Below is controller configuration screen:
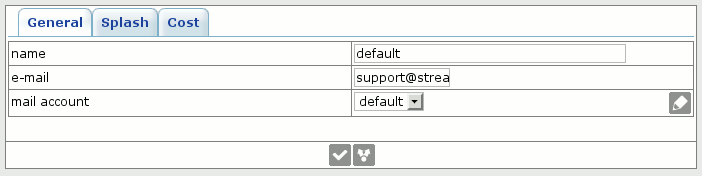
After controller is configured you should pick him up in peer's settings, for example, originator.
For this press Originators -> Edit and pick up controller from drop-down list in line origination controller.
Theory of operation is as follows:
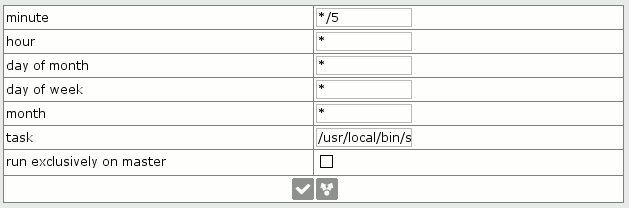
1. Origination controller is launched periodically with period, which is specified in Tasks with parameter -s, which determines period of launch.
Therefore, you should add controller launch to Tasks to activate this feature.
Application, which performs origination control, is named origination_controller.
An example of application run: /usr/local/bin/smartswitch/origination_controller -s 5.
This means, that period of launch is 5 minutes.
The period of launch in Tasks should match with -s parameter.
An example of application launch in Tasks:
2. When run, application finds all peers, on which origination controllers are configured and performs handling of each peer separately.
3. Splash control
Is performed, if fields in Splash tab are filled
4. Cost control.
Is performed, if fields in Cost tab are filled.