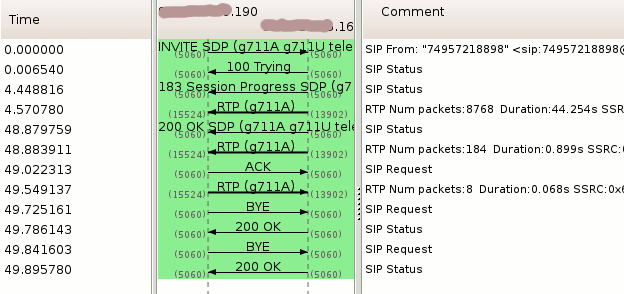
Suppose you want to get call graph in convenient format for debugging.
A wireshark application does this:

Clicking on each arrow you can get call graph:
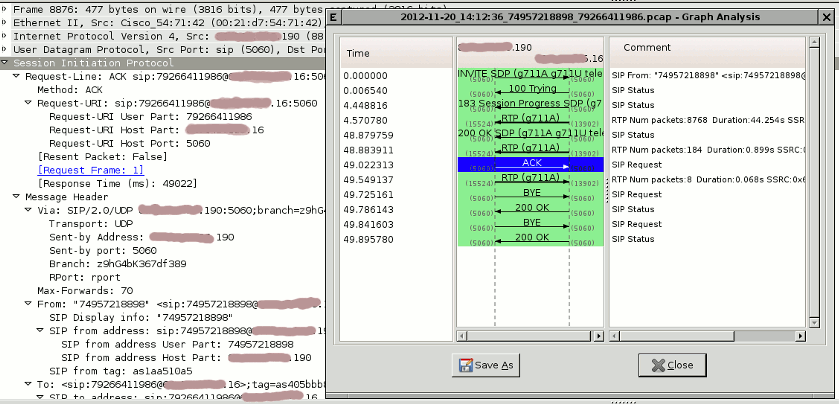
Wireshark requires file, that contains captured call in .pcap format.
Therefore our purpose is to get this file.
This is preferred way.
Use embedded system of Call capturing to get .pcap file.
In case if for some reason automatic Call capturing is not available in your version, use manual method.
1. Acquire root access as described in chapter How to acquire root access
2. Get packet dump of a call.
For this we use tcpdump utility:
# tcpdump -s 0 -w voip.cap
This command will capture packet dump to file voip.cap in current directory.
However much better if you know, where from you will get traffic or where to you will send traffic.
IP address of terminator or originator you can see on web-interface.
In this case execute command this way:
# tcpdump -s 0 -w voip.cap host 192.168.0.1
In this case 192.168.0.1 - is IP address of needed peer, which is used for call pass-through.
To capture from several hots (for example, originator and terminator) use this instruction:
# tcpdump -s 0 -w voip.cap host 192.168.0.1 or 192.168.0.2
In this case 192.168.0.1 - is the IP address of originator,
192.168.0.2 - is the IP address of terminator.
The commands above capture on the first network interface from the list of system's interfaces.
To capture on specific network interface execute command this way:
# tcpdump -i rl0 -w voip.cap
Here, rl0 - is one of interfaces displayed from
# ifconfig
The commands above begin capturing packet dump.
To stop dumping and logging to file press CTRL+C.
Attention! To capture call correctly you need to launch tcpdump before the call start and stop after call end.
3. Download packet dump to your PC.
For this you should use pscp application (http://www.chiark.greenend.org.uk/~sgtatham/putty/download.html):
> pscp.exe -C admin@10.0.0.1:voip.cap voip.cap
Now you have packet dump on your PC.
Open packet dump, obtained via automathic or manual method, in wireshark application (http://www.wireshark.org/).
For this: